Secure Access Overview
The Cisco Secure Access Overview dashboard lists the latest information about your organization. The Overview dashboard displays information about your organization's traffic and the amount of data transferred over your connections and correlates this with security events.
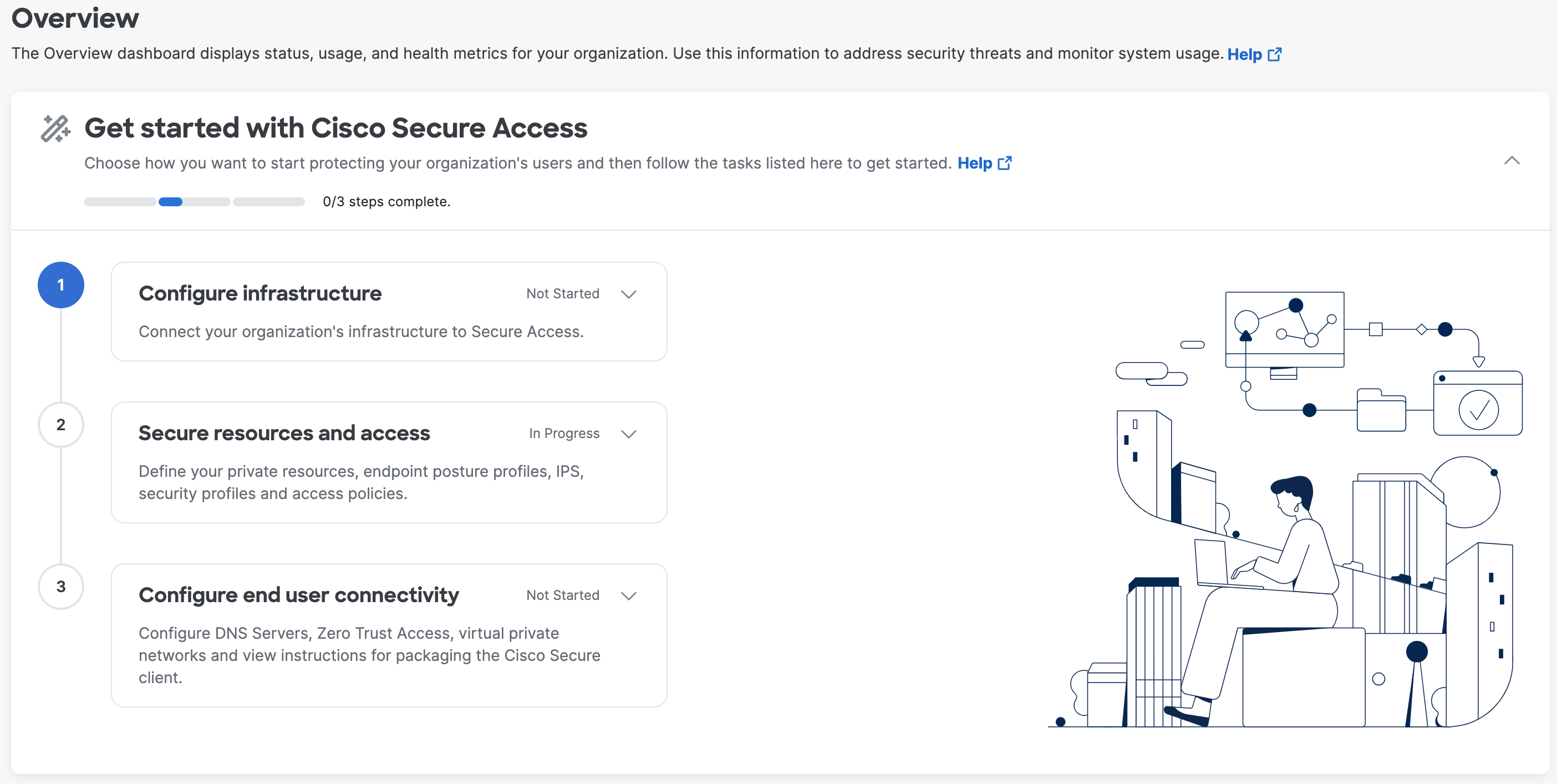
From the Overview dashboard, you can set up Secure Access through the Get Started with Secure Access workflow. If you have established network connectivity, the first workflow is completed and lists your network connections. For more information about Secure Access workflows and how to start, see Begin Secure Access Onboarding Workflow.
Once you configure your organization's network connectivity, confirm that traffic from user devices can reach Secure Access. For information about the Secure Access reports, see Get Started with Reports.
Table of Contents
- Prerequisites
- Get Started Workflow
- Connectivity
- Data Transfer
- Security
- Users and Groups
- Private Resources
Prerequisites
- A minimum user role of Read Only. For more information, see Manage Accounts.
Get Started Workflow
The Getting Started with Secure Access Workflow describes the first configuration steps required to begin protecting your systems with Secure Access.
Connectivity
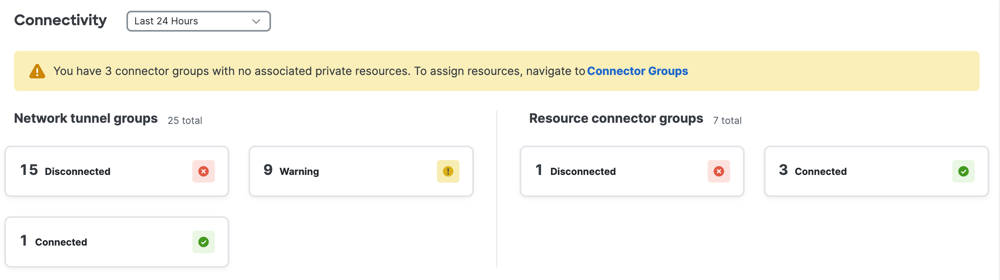
The Connectivity section describes the status of your organization's configured Network Tunnel Groups and Resource Connector Groups.
Data Transfer
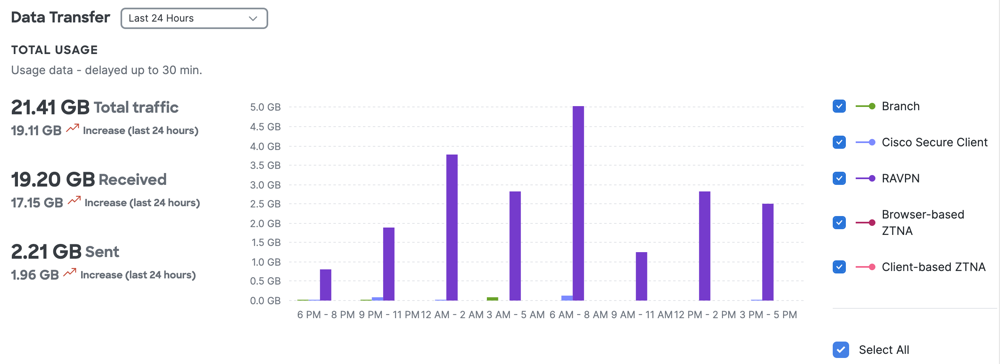
The Data Transfer section describes the total traffic, and the amount of data received and sent over the networks in your organization. Filter the usage data by the source to identify trends related to the type of connectivity:
- Branch
- Cisco Secure Client
- Remote access virtual private network (RAVPN)
- Browser-based Zero Trust Network Access (ZTNA)
- Client-based Zero Trust Network Access (ZTNA)
Security
The Security section includes information about the security activity (requests and blocks) and top security categories visited by devices and users in your organization.
Security Activity
The Security > Security Activity section displays the number of access events—requests and blocks. It also displays the number IPS events—signature events.
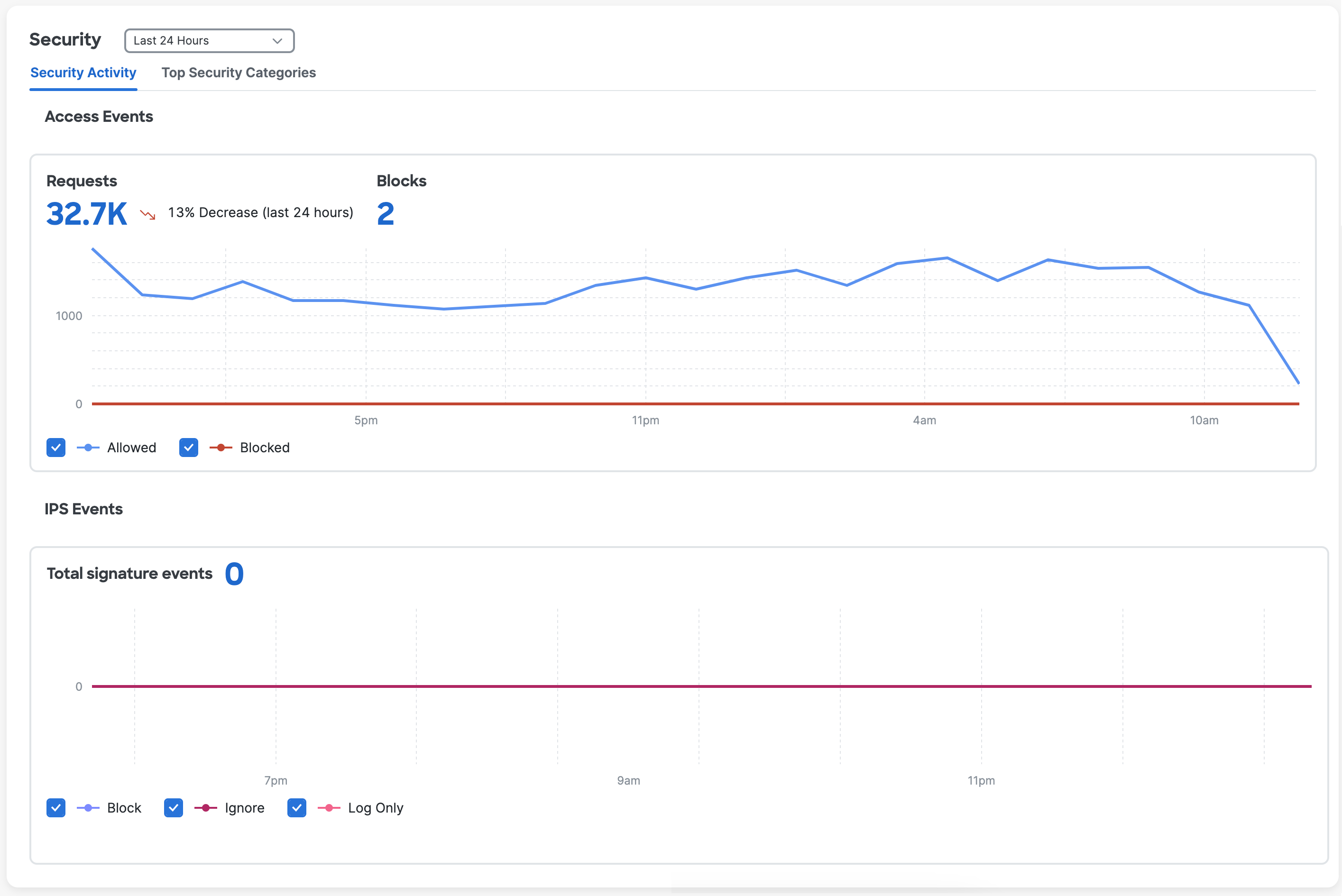
The Security > Security Activity > IPS Events section displays an expiry banner when a certificate for Private Resource Decryption has expired or will expire within 90 days.
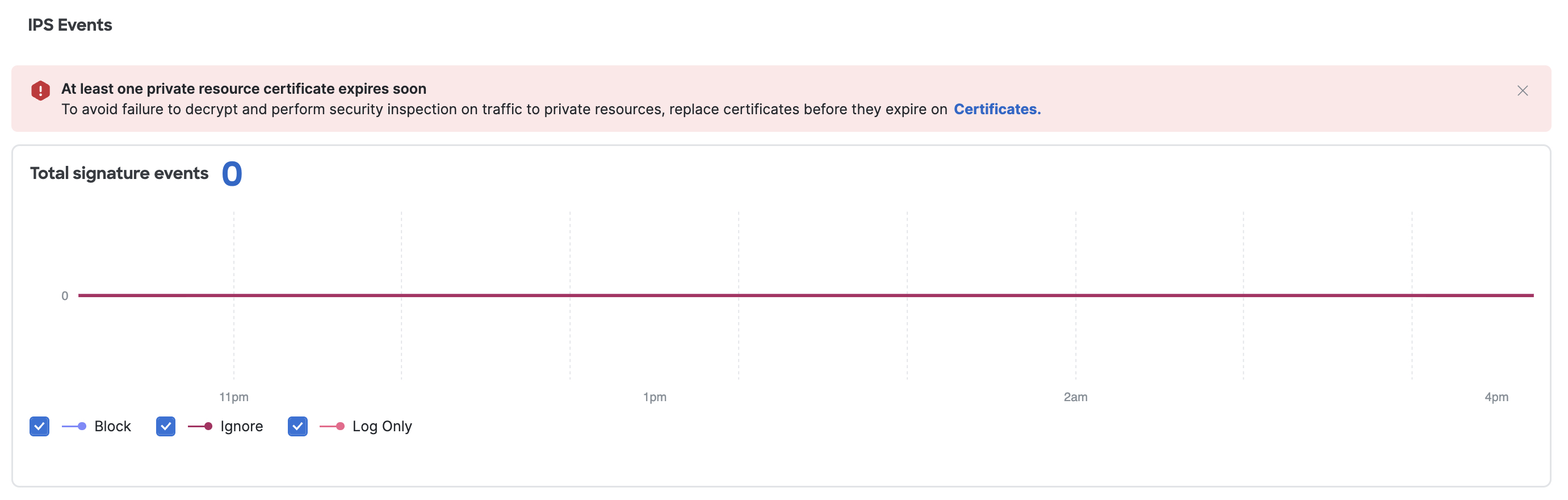
Users with the Full Admin or Security Administrator role can follow the Certificates link to update the certificate, or close the banner. If the certificate is not updated, a closed banner will reappear the next time the user opens the Overview page.
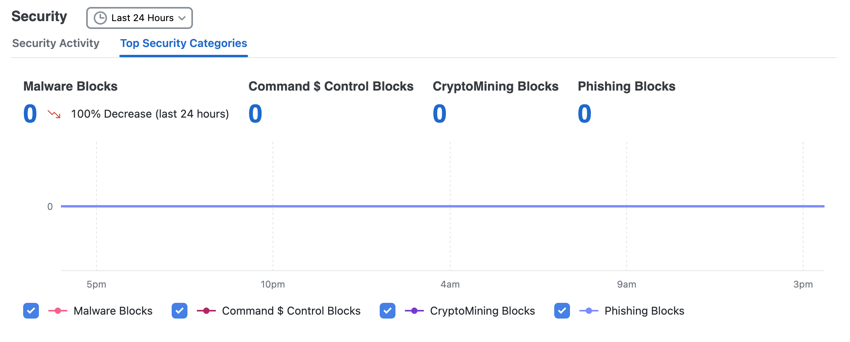
Top Security Categories
The Top Security Categories displays the number of requests to the top security categories.
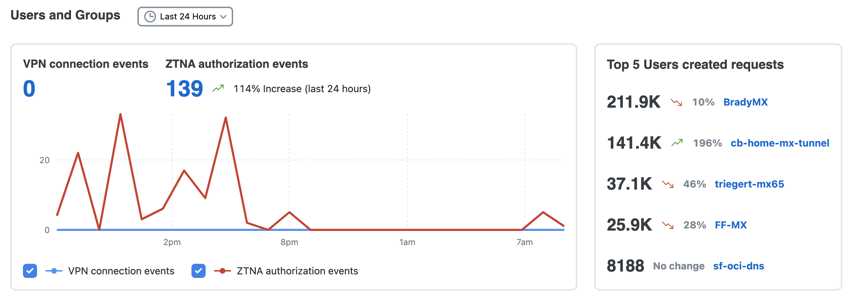
Users and Groups
The Users and Groups section displays the number of virtual private network (VPN) connections and Zero Trust Network Access authorization events over time. This section also lists the top users in your organization who made the greatest number of requests in the selected time period.
Users and Groups displays expiry banners for certificates that impact user authentication and access when:
- A certificate has expired
- A certificate will expire within 90 days
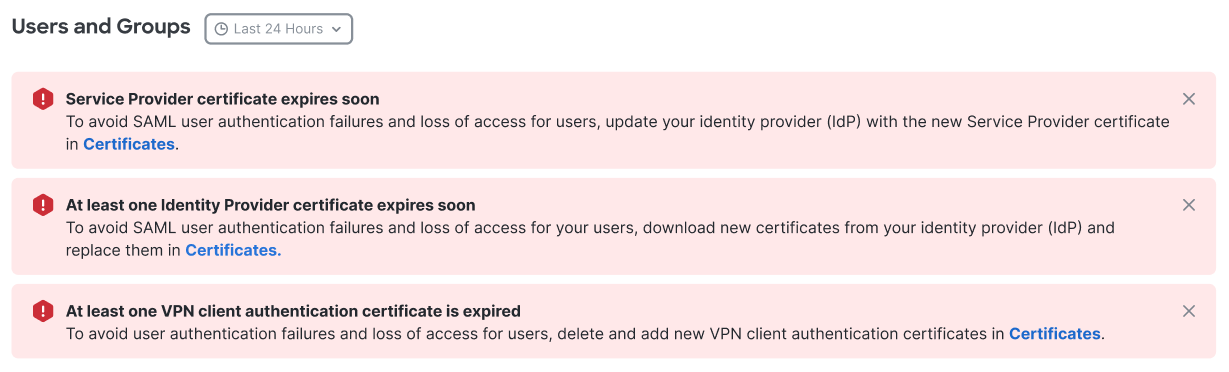
Users and Groups certificate expiry banners apply to three certificate types:
- Manage SAML Certificates for Service Providers
- Manage SAML Certificates for Identity Providers
- VPN Certificates for User and Device Authentication
Users with the Full Admin or Security Administrator role can follow the Certificates link to update the certificate, or close the banner. If the certificate is not updated, a closed banner will reappear the next time the user opens the Overview page.
Private Resources
The Private Resources section displays the number of times applications are requested, the number of unique active users that request access, and the number of requests that are allowed or blocked over the selected time period.
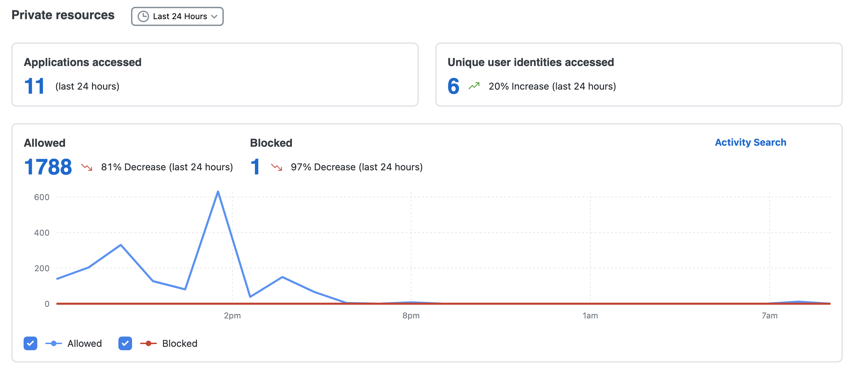
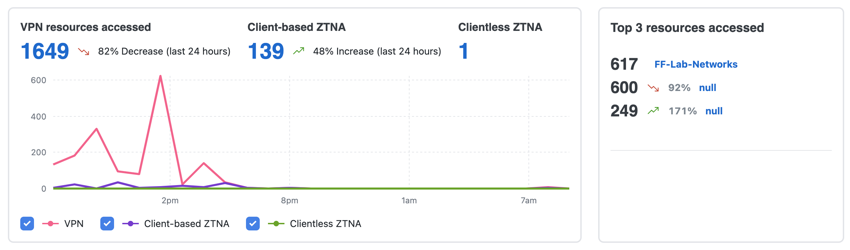
The Private Resources section also displays the number of times remote users connected to Secure Access and the method of the connection: virtual private network (VPN),client-based ZTNA, or clientless ZTNA. The section also includes the top resources that received traffic.
Step 4 – Configure Endpoints and Network Sources < Secure Access Overview > Quickstarts
Updated 3 months ago
