View Security Events
The Security section of the User Dashboard displays user-specific security events including rules and allowed/blocked events.
- Note: Data displays in the Security section only if the user is enrolled in Zero Trust Access.
Events are generated for various reasons, including when a security rule is triggered. Security rules are created based on access policies that you define in Secure Access to control risky and disallowed activities. For more information, see Manage the Access Policy .
Procedure
- From the left menu, navigate to: Experience Insights > Management.
- On the Endpoints summary page, click a user name.

- On the User Dashboard, scroll down to the Security section.
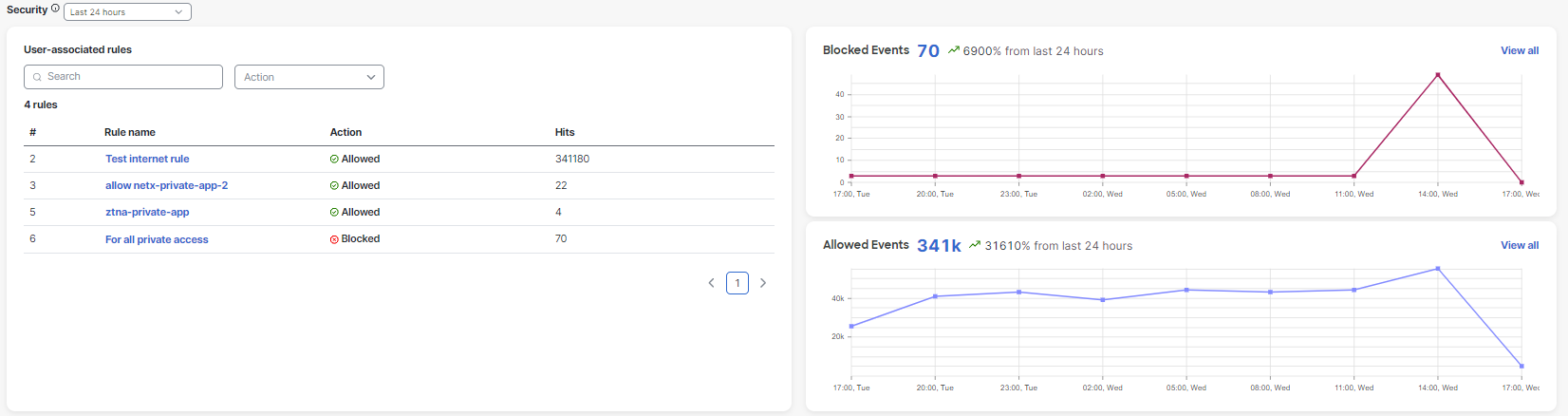
- The User-associated rules section displays the rules that triggered per the user's activity and whether the activity was allowed or blocked.
- The rule list is arranged by the priority order you set in Access Policies. For more information, see Manage the Access Policy .
- The Blocked Events and Allowed Events graphs display the total number of blocked and allowed events for the user within a specified time period.
- To see a comprehensive view of events that are associated with the user, click View all .
View User and Device DetailsView Security Events View Device Path to Secure Access
Updated about 3 hours ago
