Use Search and Advanced Search
Use Search and Advanced Search to filter event details. For example, search for events with specific domains but exclude subdomains you are not interested in.
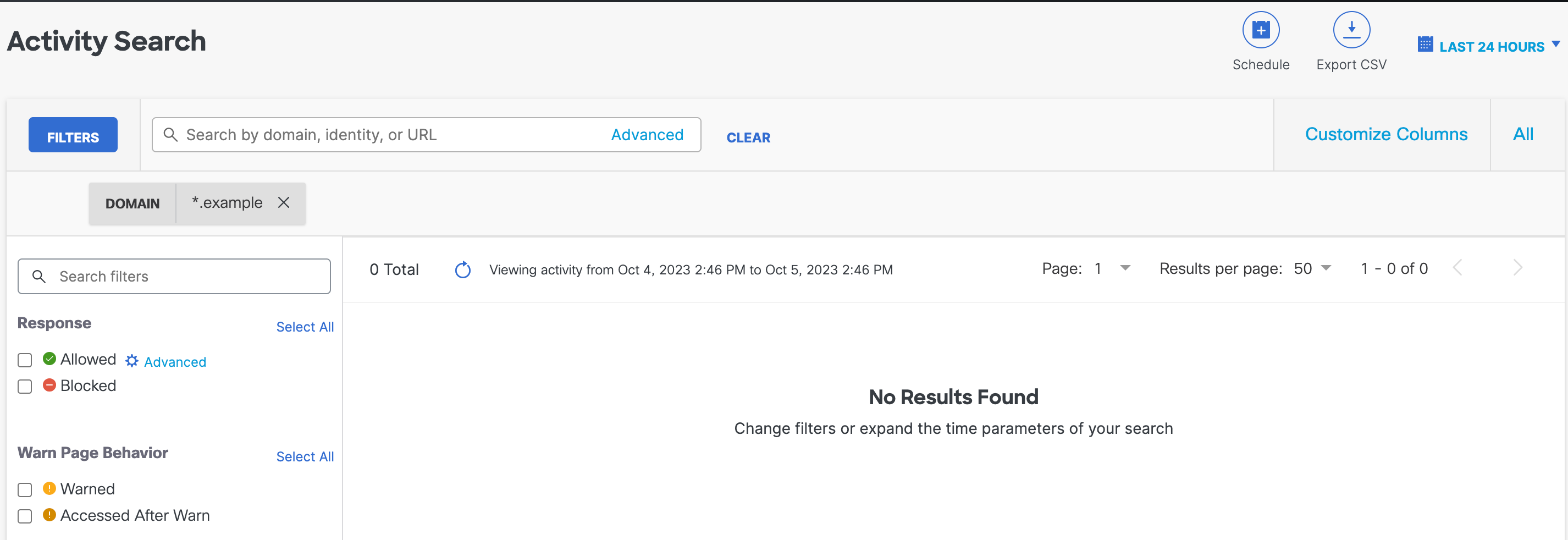
Wildcards are available for some fields (domains, URLs, and file names) to search for varieties within that field. For example, use *.gif in the file name to search for all .gif files.
Table of Contents
Packages and Feature Availability
Features are available based on your Secure Access package. Find your package at Admin > Licensing. For more information, see Determine Your Current Package. If you don't have access to a feature, contact your sales representative.
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
Search
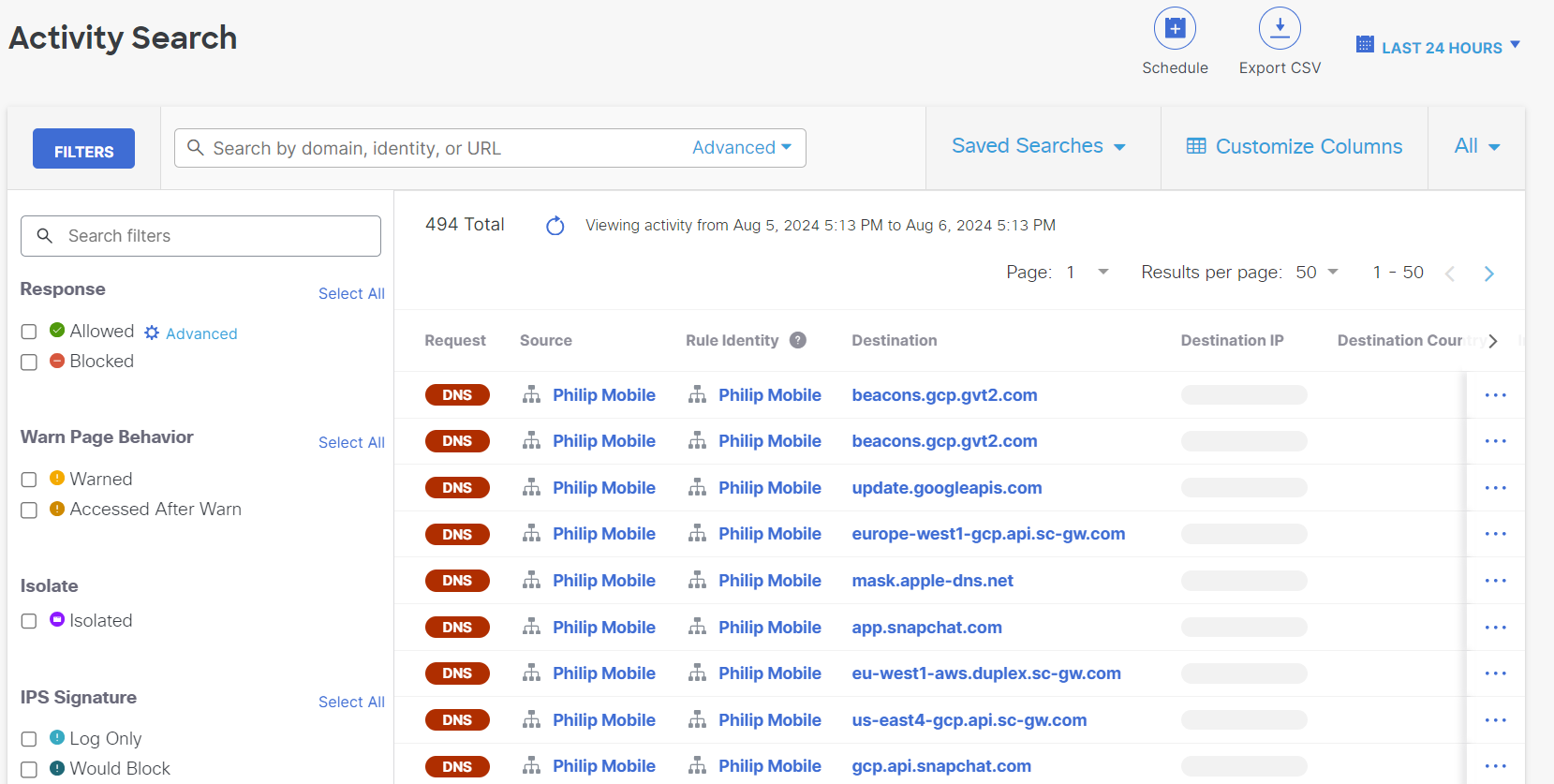
Search the report for domains, identities, or URLs. To search and filter the report by more options, such as threat type or file name, use Advanced Search.
Wildcards
Domains
Domains can be searched in the search bar or advanced search with the wildcard * to include or exclude subdomains.
For example, example.com will search the top-level parent domain of Example, *.example.com will search for only the subdomains of Example, and *example.com will search for both the parent and subdomains of Example.
You can use wildcards to search by top-level domain.
For example, *.example will search for all top-level domains that end in .example.
URLs
The wildcard * can be used in any part of the URL path to search for URLs containing certain terms.
For example, example* will search for URLs containing "example".
File Names
File names can use the wildcard * to search for file types, in Advanced Search only. For example, *.gif will search for all files that are .gifs.
Advanced Search
- In the search bar, click Advanced.
- In the Advanced Search window, complete the fields:
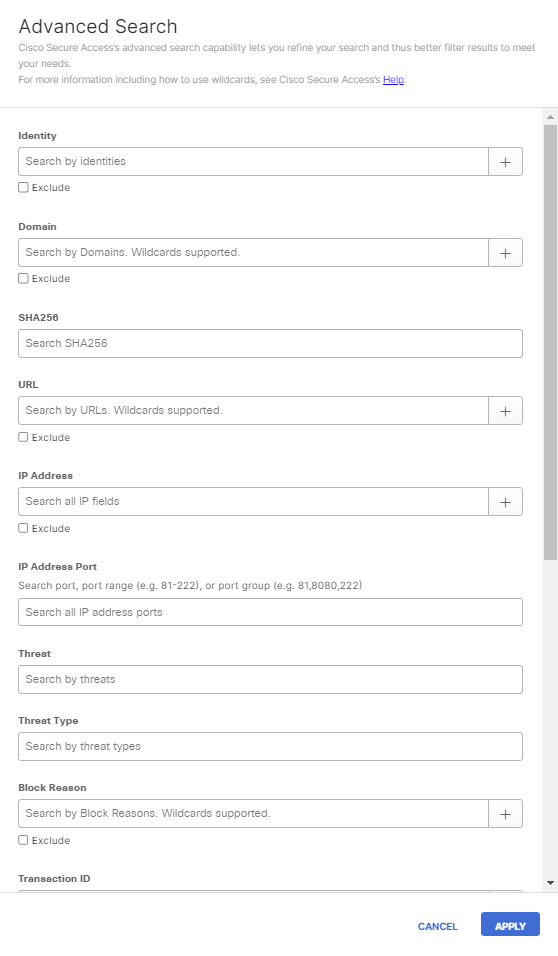
- Identity—Include or exclude sources from your search. Secure Access opens a menu listing sources as soon as you begin typing.
- Domain—You can search for more than one domain at a time. When you add a domain, a new field appears so that you can add or exclude another domain.
- SHA256—Search by the hash function.
- URL—Search by specific URL path.
- IP Address—Search for events associated with IP addresses on your network (either internal or public egress IP address). This does not provide the capability to search for destination IP addresses.
- IP Address Port—Search by a firewall port number.
- Threat—Search by threats.
- Threat Type—Search by threat type. For more information, see Threat Category Descriptions.
- Block Reason—Search by the details of a block request.
- Transaction ID—Search by any transaction ID
- Public Application—Search by any public application.
- Resource/Application—Search by any resource or application available in the drop-down.
- Application Group—Search by any application group available in the drop-down.
- OS Type — Search by operating system from which activity originated.
- Location — Search by the location from which activity originated.
- Egress IP Type — Search by the egress IP addresses: shared or reserved.
- Egress Data Center — Search by the egress data center location from which activity originated.
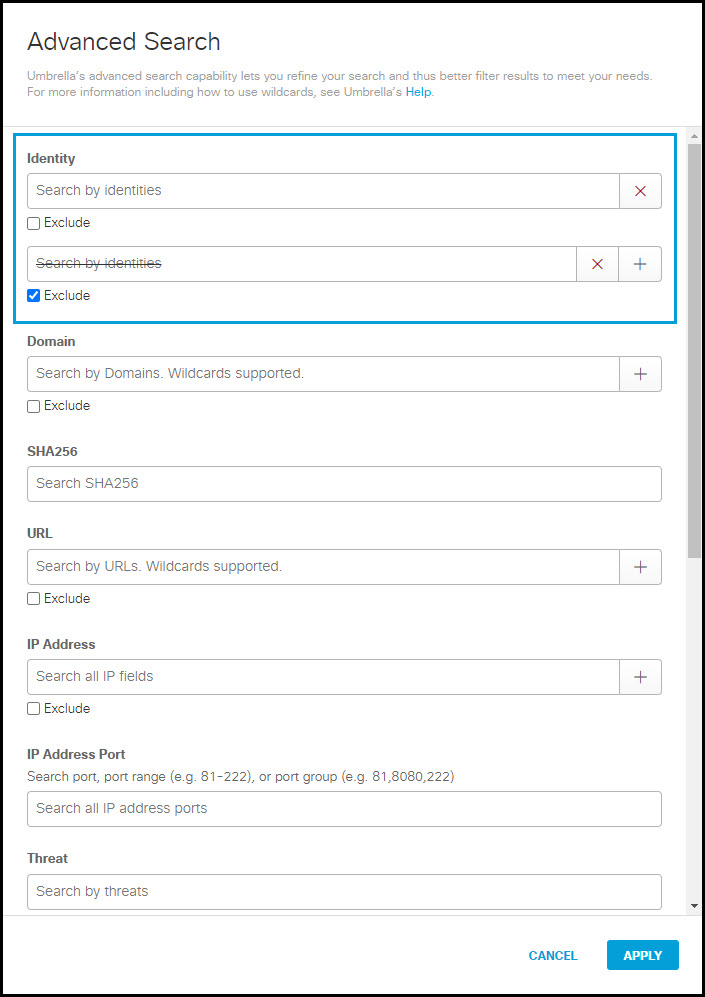
- In the Advanced Search pop-up window, add search parameters and click Apply.
- Identity—Include or exclude sources from your search. Secure Access opens a menu listing sources as soon as you begin typing.
- Domain—You can search for more than one domain at a time. When you add a domain, a new field appears so that you can add or exclude another domain.
- SHA256—Search by the hash function.
- URL—Search by specific URL path.
- IP Address—Search for events associated with IP addresses on your network (either internal or public egress IP address). This does not provide the capability to search for destination IP addresses.
- IP Address Port—Search by a firewall port number.
- Threat—Search by threats.
- Threat Type—Search by threat type. For more information, see Threat Category Descriptions.
- File Name—Search by the name of a file.
- OS Type — Search by operating system from which activity originated.
- Location — Search by the location from which activity originated.
- Egress IP Type —Search by the egress IP addresses: shared or reserved.
- Egress Data Center —Search by the egress data center location from which activity originated.
Schedule an Activity Search Report < Use Search and Advanced Search > Security Activity Report
Updated 6 months ago
