Multiple Active Directory and Secure Access Sites
Secure Access sites let administrators segregate their Secure Access deployments. Each Secure Access site is an isolated deployment in which components only communicate with other components in the same Secure Access site. Secure Access sites are a container to isolate sections of a large multi-site network into groups which only sync to the other components in the container. For example, Secure Access sites may be North America, Asia, and Europe or Northeast, California, Atlanta office, South Region, and London, and each Secure Access site may be one or a combination of Active Directory (AD) sites.
This is primarily useful in AD environments containing locations with high-latency connections, or in environments with locations whose internal IP space overlaps.
Table of Contents
Active Directory Sites and Secure Access Sites
A site represents a set of computers connected by a high-speed network, such as a local area network (LAN). Typically, all computers in the same physical site reside in the same building or perhaps the same campus network. AD and Secure Access both use the term "sites," and while related, have slightly different meanings.
Active Directory Sites and Services
- For AD, a site object represents the actual directory data that is replicated between domain controllers.
- AD sites are used to manage the objects that represent the site, and the servers that reside in the site.
Secure Access Sites
- For Secure Access, a site refers to a set of components—virtual appliances (VAs), connectors, and domain controllers—that communicate only with each other.
- An Secure Access site is more than a label and is more like a container; however, is not the same as an AD site. Multiple AD sites can be part of an Secure Access site, but one AD site should not be split into multiple Secure Access sites.
- A site must have a minimum of two VAs, and one connector and DC each for AD integration.
Because Secure Access sites act as isolated deployments, each Secure Access site must have a minimum of two VAs. If AD integration is also being used, each site must additionally contain a minimum of one AD connector and ALL domain controllers against which a user in that location authenticates.
When to Use Secure Access Sites
- You need to limit WAN traffic between locations and are using AD sites to limit authentication to local servers
http://technet.microsoft.com/en-us/library/cc782048(v=ws.10).aspx. - Your locations communicate between a NAT device, which causes the internal IP address of an end machine to be lost when communicating between locations.
- Your locations use overlapping internal IP ranges.
- You have locations which have high-latency connections between them: for example, branches in different continents. High latency connections, especially between the connector and the VAs, can result in delays to updates for user mappings.
Caveats
The isolation of the components in a given Secure Access site means that a specific VA will only be aware of users who have authenticated against domain controllers assigned to the same Secure Access site. As a result, we do not recommend using multiple Secure Access sites in a single AD site, even if that AD site spans multiple geographical locations. In such a scenario, users in a location may still authenticate against a DC in a different location, and thus the Secure Access components may miss user mappings.
Use Secure Access Sites
Individual Secure Access sites should be configured as if they are complete deployments. For each Secure Access site:
- Follow the previous steps of this guide again, and after each sub-step, to verify that the component has synced or reported to the dashboard, assign the component to a site by clicking its name and selecting an existing site or creating a new site.
- You may also rename the default or any existing sites.
Important
Ensure that there are at least two VAs, one AD server and one AD connector assigned to each site. Verify a complete, functioning deployment at each site before moving on to the next site.
Assign a Site to a Component
- Navigate to Connect > Users and Groups > Configuration Management.
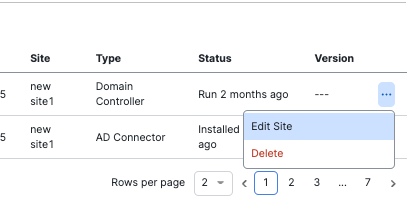
- Select Active Directory. Next to the component you wish to change, click the ellipsis (...) 3 three dots, and then click the Edit Site icon. The Site modal appears.
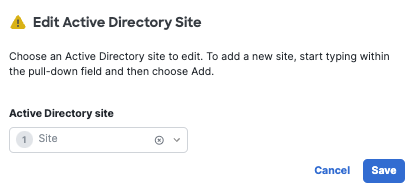
- From the Site drop-down list, select a site and click Save.
Active Directory Only
If you change the location of a virtual appliance, Cisco AD Connector, or domain controller after you've installed the connector service, you must Stop/Start the connector service on each connector at both the new and old Secure Access sites through the Services management tool in Windows.
Connect Active Directory to Umbrella VAs < Multiple Active Directory and Secure Access Sites > Change the Connector Account Password
Updated 6 months ago
