View Zero Trust Events in Activity Search Report
The Activity Search report includes details about Zero Trust Access traffic events in your organization. For more information about the Activity Search report, see View the Activity Search Report.
Table of Contents
Prerequisites
- A minimum user role of Read-only. For more information, see Manage Accounts.
Procedure
- Navigate to Monitor > Reports > Activity Search.
- In the top-right corner, in the Last 24 Hours menu, select a time frame for the report.
- _From the Requests menu, choose a request type or the default of All.
- In a row, click the ellipsis and choose View Full Details.
- In the Event Details window, view the Zero Trust Access event details.
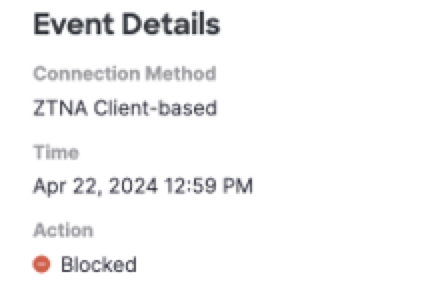
| Field Name | Description |
|---|---|
| Connection Method | The type of connection method: ZTA Client-based or ZTA Browser-based. |
| Time | The time of the event. |
| Action | Indicates if the traffic was blocked or allowed. |
Access Details
View the Zero Trust access details in the Activity Search report.
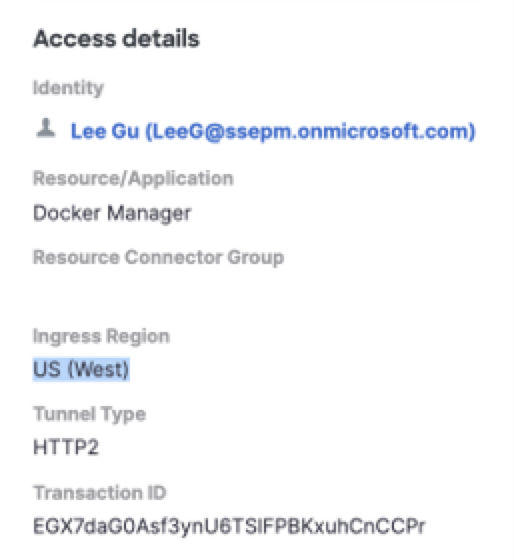
| Field Name | Description |
|---|---|
| Identity | The name and email of the user identified in the Zero Trust connection event. |
| Resource/Application | The name of the private application. |
| Resource Connector Group | The ID of the resource connector group that provides access to the private resource. |
| Ingress Region | The geographic region of the data center where Secure Access received the incoming traffic. |
| Tunnel Type | The type of traffic supported by the network tunnel, which the endpoint established with the proxy. The transport protocol on the tunnel is either HTTP or HTTP3. |
| Transaction ID | The unique ID associated with the Zero Trust connection request. Use the transaction ID to correlate and troubleshoot connection issues. |
Block Details
View the Zero Trust block details.
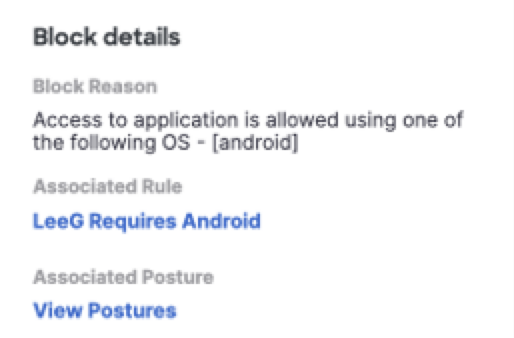
| Field Name | Description |
|---|---|
| Block Reason | Secure Access provides an explanation for blocking access to the private resource. |
| Associated Rule | When access was blocked for not meeting access or posture requirements, Secure Access reports the closest matched policy rule that would have allowed access. |
| Associated Posture | The posture profile that is configured for the associated rule. |
Endpoint Details
View the Zero Trust endpoint details.
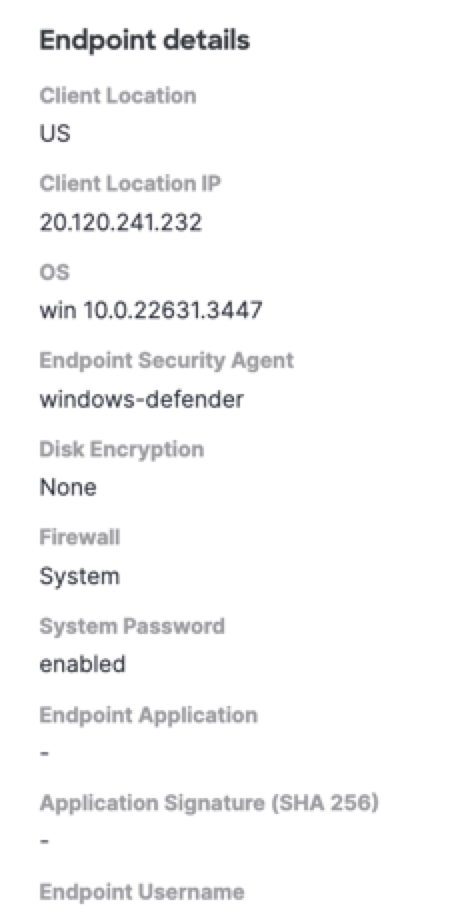
| Field Name | Description |
|---|---|
| Client Location | The two-character country identifier. |
| Client Location IP | The IP of the client. |
| OS | The operating system of the client's device. |
| Endpoint Security Agent | The name of the endpoint security agent. |
| Disk Encryption | Indicates if the client's device has disk encryption. |
| Firewall | Indicates if the client environment has a firewall enabled. |
| System Password | Indicates if the client has a system password enabled. |
| Endpoint Application | The name of the endpoint application, which initiated the connection. |
| Application Signature | The SHA256 signature of the endpoint application process. |
| Endpoint Username | The username that is associated with the endpoint application process. |
View and Customize the Activity Search Report < View Zero Trust Events in Activity Search Report > View Activity Search Report Actions
Updated 6 months ago
