Add a Security Profile for Internet Access
A Cisco Secure Access Security profile is a set of security controls and other settings that you can use in access rules.
For information about each of the components or controls that you can configure in a Security profile for internet access, see Security Profiles for Internet Access.
Table of Contents
- Prerequisites
- Procedure
- View Security Profiles
- Configure Additional Security Options
- Add a Security Profile on Internet Access Rules
- Edit a Security Profile
- Delete a Security Profile
Prerequisites
- Full Admin user role. For more information, see Manage Accounts.
- In Secure Access, configure the components that you will select in a security profile for internet access.
- Add a Do Not Decrypt list. For more information, see Add a Do Not Decrypt List for Security Profiles.
- Create the list of threat categories. For more information, see Manage Threat Categories.
- Carefully review the information about enabling file analysis with Cisco Secure Malware Analytics. For more information, see Enable File Analysis by Cisco Secure Malware Analytics.
- (Optional) Create custom notification pages that Secure Access will display when rules that use this security profile match traffic that blocks access or displays a warning. Customizations can include the logo, message, and contact information of your choice. For more information, see Notification Pages.
Procedure
Note: You can add up to 100 security profiles in Secure Access for the organization.
Configure the settings on a Security profile and add the profile to the organization. After you add the Security profile, configure any related security settings and use the Security profile in an access rule. For more information, see Configure Additional Security Options.
Add a Security Profile
-
Navigate to Secure > Security Profiles.
-
Click Add Profile, and then select Internet Access.
-
Follow the steps in this procedure to configure the settings on the security profile.
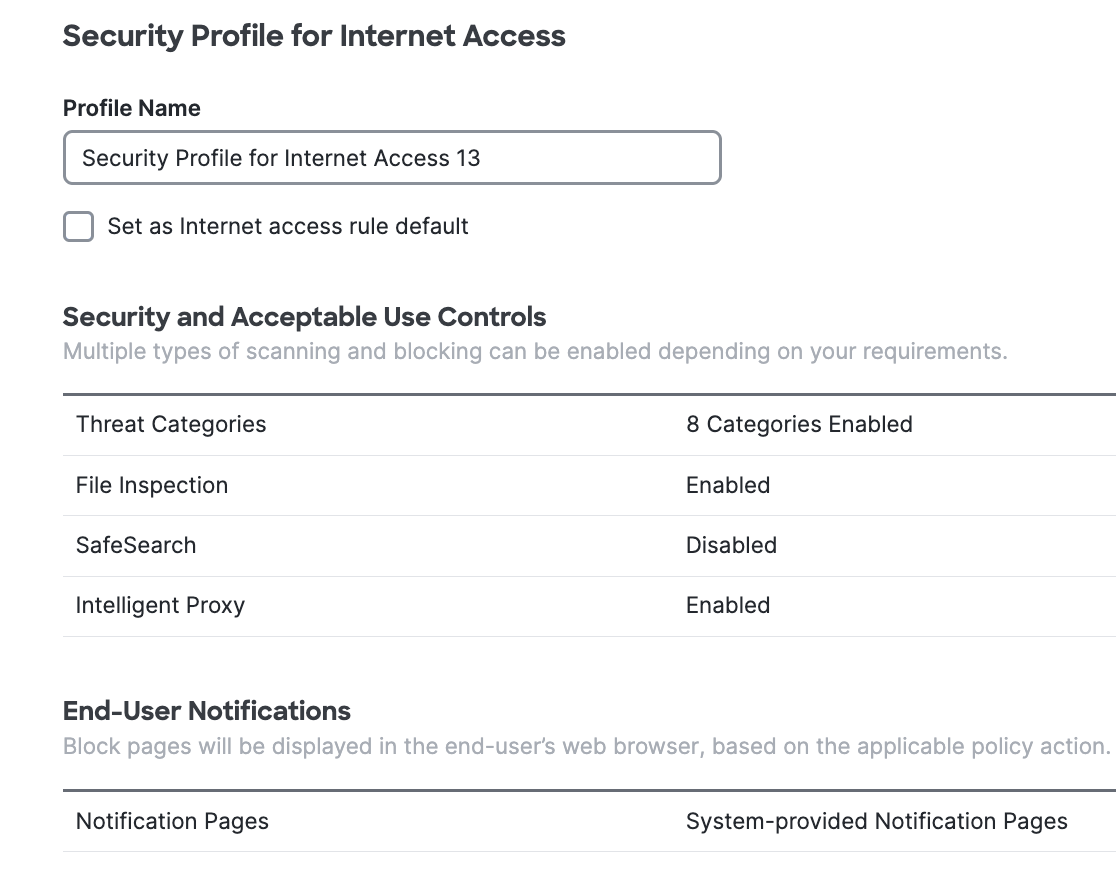
Security and Acceptable Use Controls
Configure security and acceptable use controls in the Security Profile. Depending on your requirements, you can enable multiple kinds of scanning and blocking. For information about these settings, see Security Profiles for Internet Access.
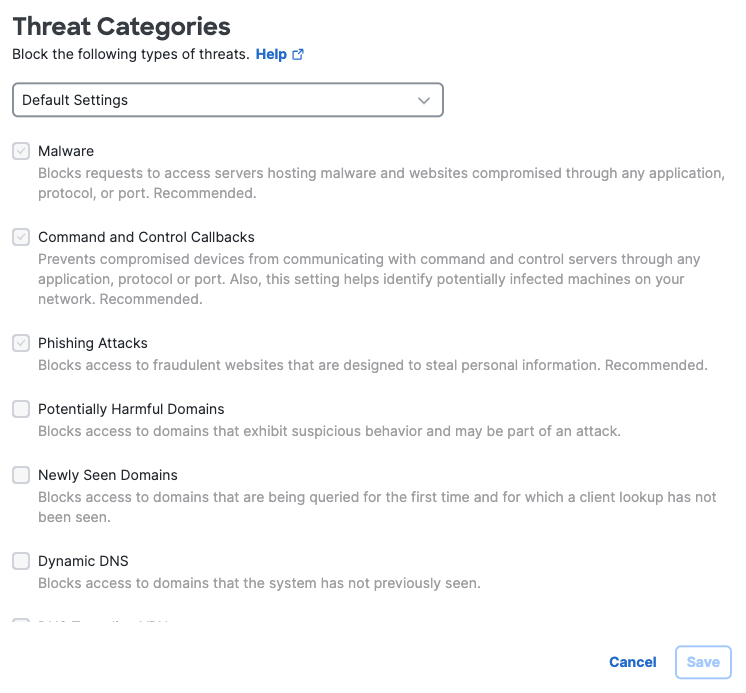
Threat Categories
-
For Threat Categories, click Edit.
-
To block access to known malicious sites and potentially risky sites based on threat category, choose from the drop-down list, one of the existing lists of threat categories. For more information on Threat Categories see, Manage Threat Categories.
-
Click Save.
File Inspection
- For File inspection, click Edit.
- Choose the file inspection and analysis tools to use to protect traffic that matches rules that use this security profile.
Important: If this is the first time you enable Cisco Secure Malware Analytics, Secure Access displays the option to select a sandbox region. Before you enable Cisco Secure Malware Analytics, we recommend that you review the instructions about this option. For more information, see Enable File Analysis by Cisco Secure Malware Analytics.
a. Click File Inspection is Enabled.
b. (Optional) Click Cisco Secure Malware Analytics is Enabled.
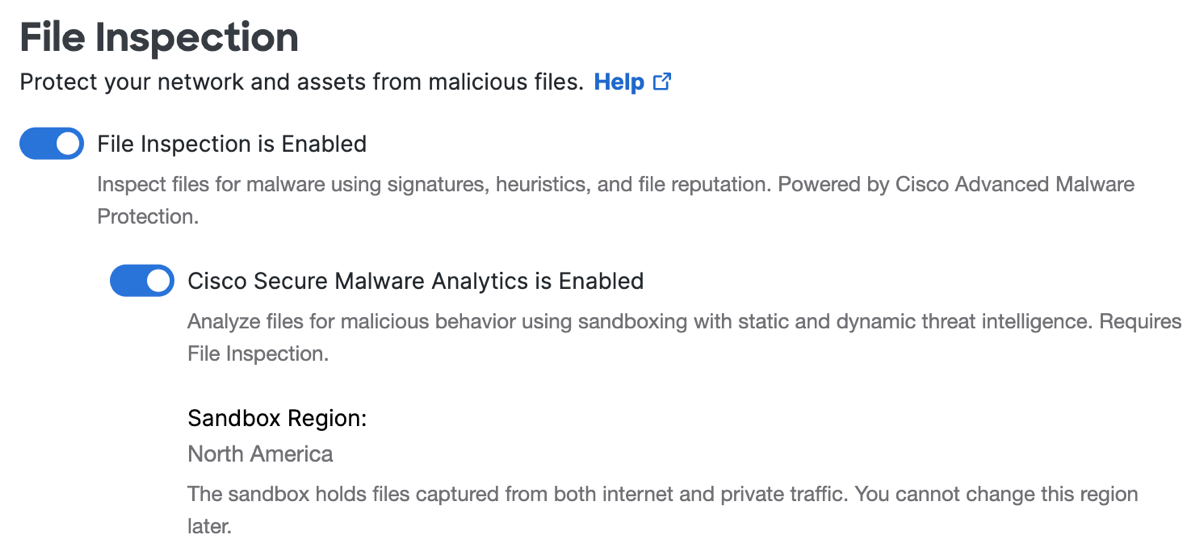
- Click Save.
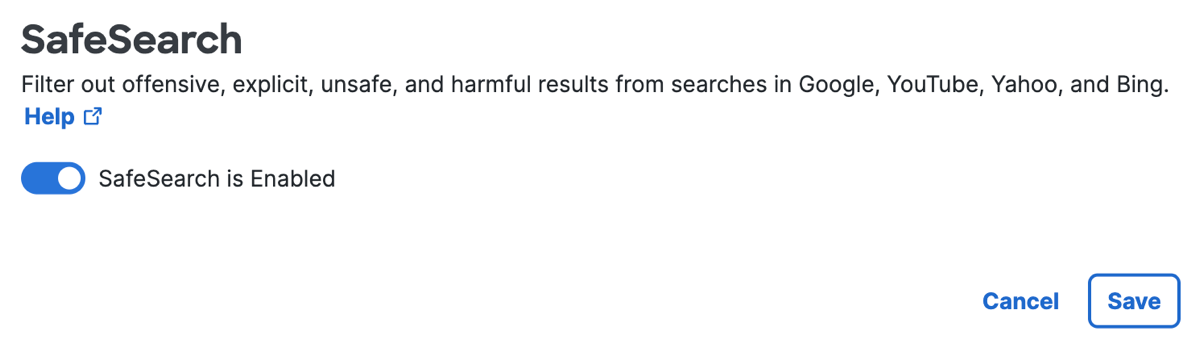
SafeSearch
-
For SafeSearch, click Edit.
-
Enable this option to filter out offensive, explicit, unsafe, and harmful search results in Google, YouTube, Yahoo, and Bing.
-
Click Save.
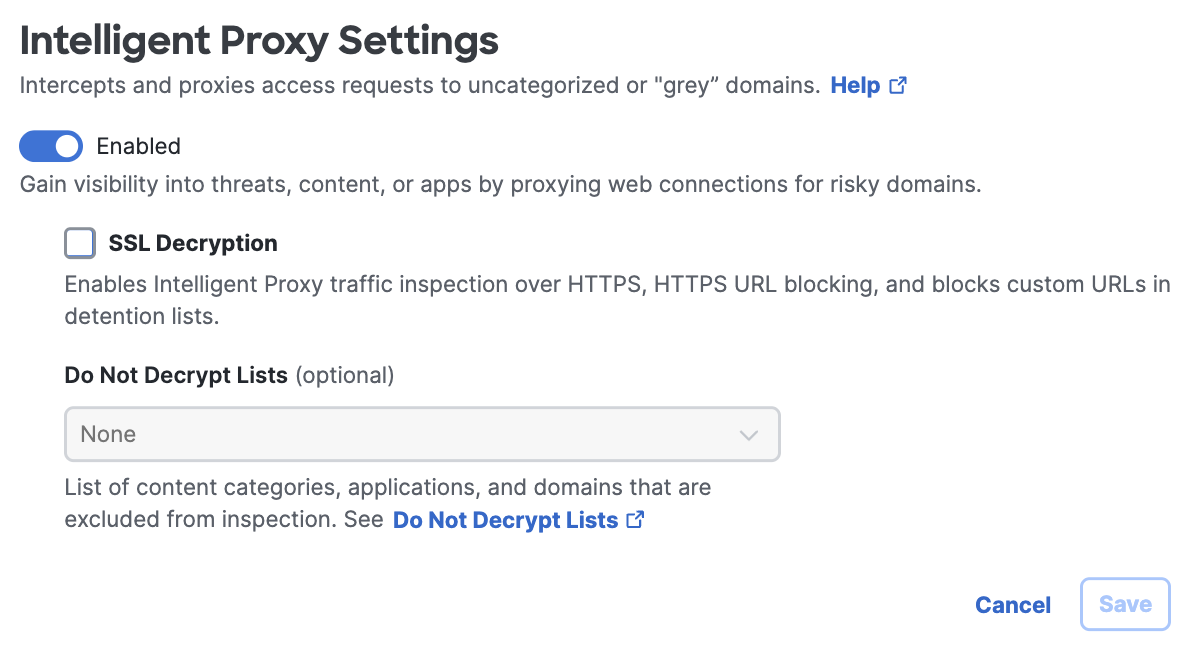
Intelligent Proxy
- For Intelligent Proxy, click Edit.
- Enable intelligent proxy to intercept and proxy requests for URLs, potentially malicious files, and domain names associated with certain uncategorized or unknown domains.
- Enable SSL Decryption to proxy and inspect traffic sent over HTTPS.
- You can select from the drop-down of the Do Not Decrypt List when you enable SSL Decryption. For more information, see Add a Do Not Decrypt List.
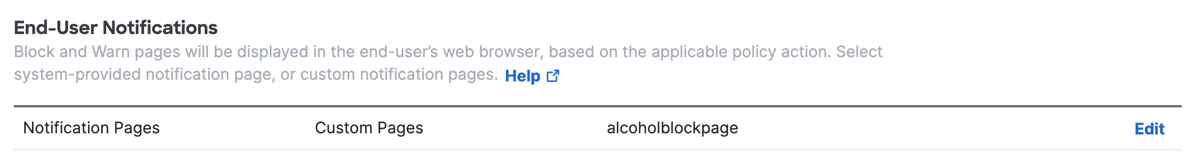
Configure End-User Notifications
Configure end-user notifications for the organization. Secure Access displays Block and Warn pages in the end-user's web browser. The display of the Block or Warn page is based on the action that you configure in each rule where the security profile is used. For more information, see Manage Notification Pages.
-
Navigate to End-User Notifications.
-
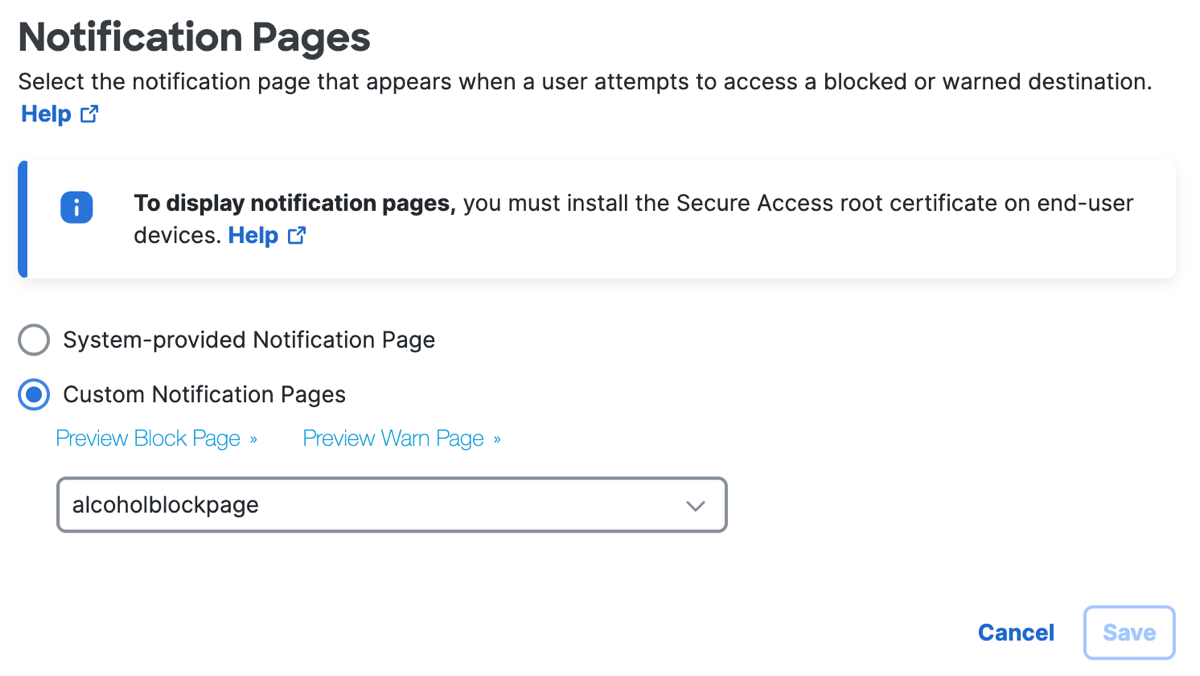
Navigate to Notification Pages, and then click Edit.
-
Choose one of the options.
Each option includes a Block notification and a Warn notification.a. Click System-provided Notification Pages.
b. Click Custom Notification Pages.
Note: For custom pages, choose the pages that you want to display. -
(Optional) To preview the pages that you have selected, click the Preview links.
-
Click Save.
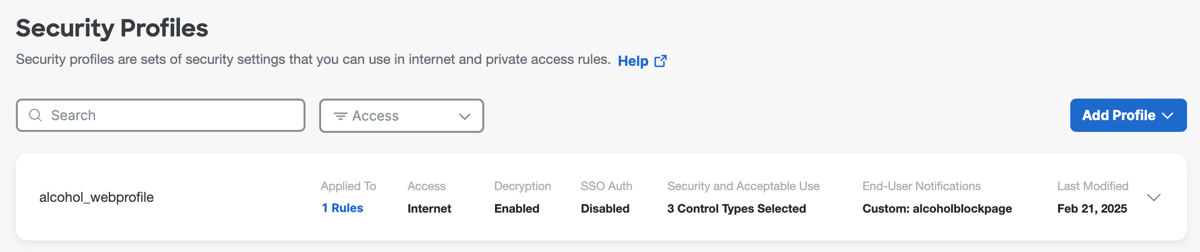
View Security Profiles
View the configured security profiles in Secure Access.
-
Navigate to Secure > Security Profiles.
-
Navigate to a security profile and expand the profile.
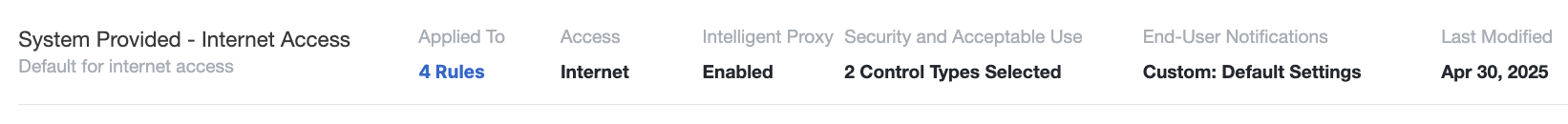
A configured security profile includes these details:- Name of the security profile.
- Applied To—The number access rules where the security profile is included.
- Access—The type of the security profile.
- Intelligent Proxy—Specifies whether decryption is enabled on the profile.
- Security and Acceptable Use—Lists the number of security controls that are enabled on the profile.
- End-User Notifications—Lists the type of notifications that are configured on the profile.
- Last Modified—The date when the security profile was last updated.
Configure Additional Security Options
Configure additional functionality that is required for your selected features. For example, configure:
- Traffic decryption
Decryption requires certificates. For more information, see Certificates for Internet Decryption. - Notification pages
To display notification pages, you must install a Cisco root CA certificate on all end-user devices. This may not be the same certificate you use for decrypting internet traffic. For more information, see Certificates for Internet Decryption.
Add a Security Profile on Internet Access Rules
Add the security profile to one or more internet access rules. For more information, see Add an Internet Access Rule and Default Settings for Internet Access Rules.
Edit a Security Profile
After you add a security profile in Secure Access, you can modify it.
- Navigate to Secure > Security Profiles.
- Expand a security profile, and then click Edit.
- Choose any of the security controls and settings to modify.
For more information, see:
Delete a Security Profile
After you add a security profile in Secure Access, you can remove it.
-
Navigate to Secure > Security Profiles.
-
Expand a security profile, and then click Delete.
-
Confirm the removal of the security profile.
a. Click Delete to confirm the removal of the security profile.
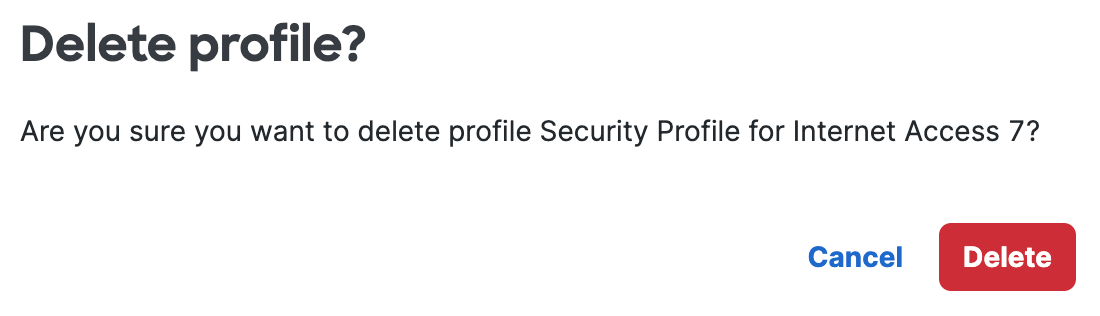
b. If the security profile is in use on an access rule, you can not remove the profile.
First remove the security profile from the access rules where it is included, and the try to remove the security profile again.
Security Profiles for Internet Access < Add a Security Profile for Internet Access > Enable SafeSearch
Updated 6 months ago
