Add a Network Identity
You register a fixed network to Secure Access by adding a Network identity that is configured to include the fixed network's public IP space. If the public IP space is found in an existing Network identity, you can not use the IP address to register a new fixed network. In Secure Access, all traffic originating from that IP space is identified as coming from that network. Thus, to register a network to Secure Access, you add the public IP space, or IP range, which defines the scope of the identity.
For Network identities, Secure Access supports both IPv4 and IPv6 IP addresses.
Once you've registered a network by adding a Network identity, you build policies to extend Secure Access protection to any device that connects to the internet from behind that network. For more information about policies, see Manage Policies.
Table of Contents
Prerequisites
- Full Admin access to the Secure Access dashboard. See Manage Accounts.
- Your network's IP address must be unique within Secure Access.
- Determine if you have a dynamic IP address. Dynamic IP addresses are only supported for IPv4. Most home, small school, and small business networks are typically provisioned by Internet Service Providers (ISPs) with a dynamic IP address (IPv4) when defining each unique internet network. For more information, see IPv4 dynamic IP address.
Procedure
To start protecting your network, complete the following steps.
- Step 1 – Select the Appropriate Network
- Step 2 – Set up the Network Identity
- Step 3 – Change the DNS Settings on Your Relevant Network Device
- Step 4 – Test Your Network
Step 1 – Select the Appropriate Network
First, determine the IP address of your network.
- Go to http://www.whatismyip.com.
Your IP address and location are displayed. Both IPv4 and IPv6 IP addresses are displayed.
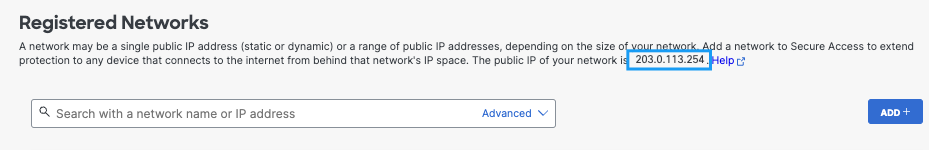
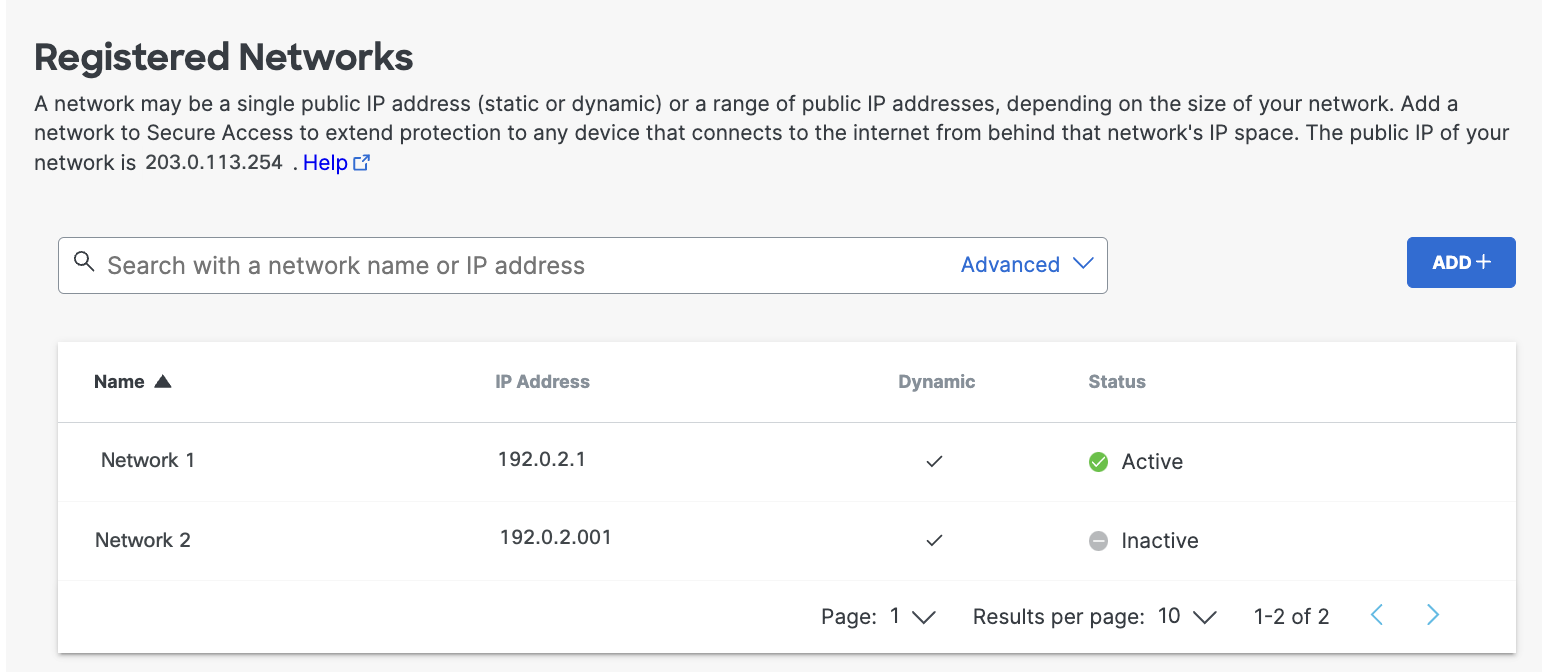
or - In Secure Access, navigate to Resources > Registered Networks.
You'll find your IP address listed at the top of the page.
Pre-registering Your Networks
If you plan to have multiple network identities, it's a good idea to immediately register all of your networks with Secure Access. Chances are that if you have more than one public egress IP in your organization, you'll have more than one network identity. Having the networks pre-registered ensures that they're available right away when you do point traffic. It also ensures that all the IP space that belongs to your company is correctly assigned in our systems. Until traffic is pointed to Secure Access DNS service, no protection is available and there is no reporting so there's no harm in adding all networks beforehand.
Note: Depending on your package, if you attempt to add a network other than the one currently being used to access the Secure Access dashboard, Secure Access may prompt you to contact Support for manual verification. If this occurs, you'll also need manual verification from Support for IPv4 ranges larger than a /29 network and IPv6 ranges than a /56 network. Verification cases are created automatically and you'll receive an update as soon as it's reviewed. If you are not sure of your current package, contact your sales representative. See also, Cisco Umbrella and Cisco Secure Access packages.
Step 2 – Set up the Network Identity
- Navigate to Resources > Registered Networks and click Add.
Note: If possible, add the network from the IP being registered; otherwise, an email is generated, which requires that a link is visited from the IP address of the network being registered.
- Give your Network identity a meaningful Network Name.
Giving your identity a good network name will help you find it easily when you later add a policy against it through the Add A Policy.
Note: Dynamic IP addresses are only supported for IPv4.
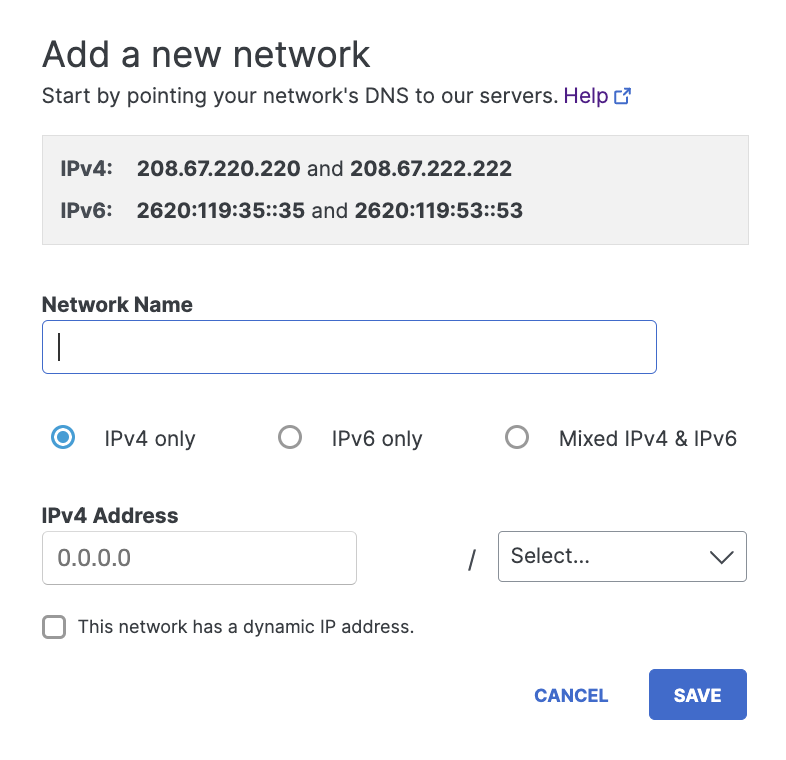
- Select an internet protocol: IPv4, IPv6, or Mixed IPv4 & IPv6.
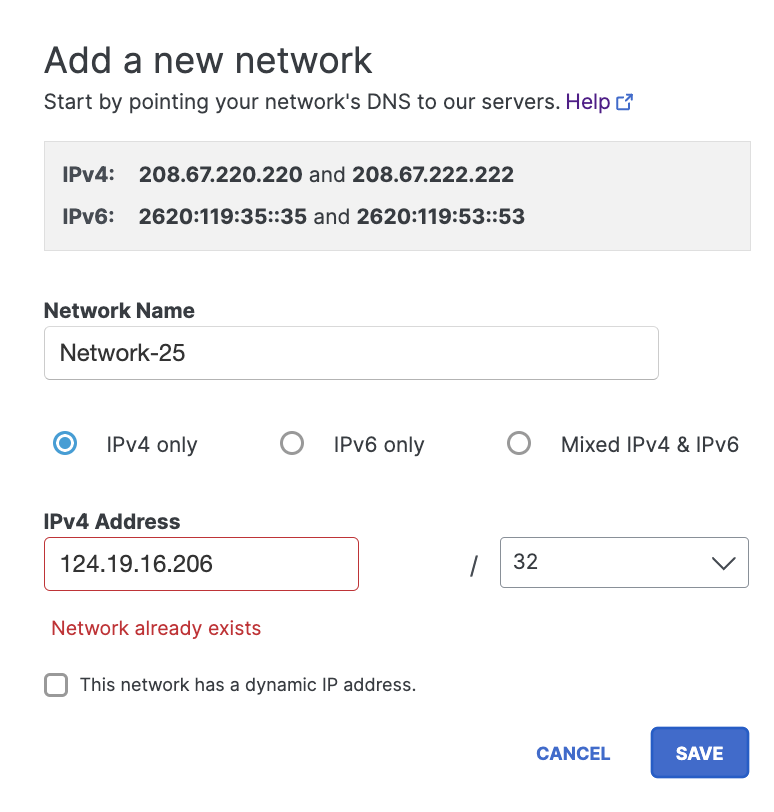
Select a protocol based on the Secure Access IP address to which you have configured your router. - Add the network's IP address and choose a subnet mask.
The network must be unique within Secure Access. If Secure Access displays theNetwork already existserror message, create a support case by contacting Cisco Secure Access Support.
- For IPv4 only, if it's a dynamic IP address, check This network has a dynamic IP address.
Note: Most Dynamic DNS (DDNS) clients work toward keeping your network updated; however, Secure Access does not support third-party DDNS clients.
Dynamic IP Address—IPv4 Only
A dynamic IP address means that the 'public' IP of your network changes over time when the 'lease' for that IP address changes. Your IP may stay the same for several weeks, but the lease will eventually expire and be given to another customer of your ISP. When the IP address you've registered with Secure Access changes, Secure Access security settings no longer apply. These settings no longer match your account information and must be updated. To avoid having to manually update this information, install the Secure Access Dynamic IP Updater on at least one computer within the network that you've registered in Secure Access. The Secure Access Dynamic IP Updater automates the discovery and registration of a network's IP address to your Secure Access account whenever the dynamic IP address changes. If you do not do this, you must manually re-enter your IP address each time it changes. For more information, see Networks with Dynamic IP Addresses.
To maintain and automatically update your IPv4 dynamic IP when it changes, following these guidelines:
- The computer should be stationary to the network and not a laptop (only used in the network on which you are configuring Secure Access).
- The computer should always be powered on or turned on before any other computers log onto the network.
- Click Save.
Once the service validates your IP address, the network is listed at Resources > Registered Networks. Initially, Secure Access lists your new network identity's status as Inactive. Network status only changes to Active when DNS traffic is sent to Secure Access from the network.
The policy applied to your new identity depends on your policy configurations. If you have a policy configured that includes network identities, Secure Access applies that policy; otherwise; Secure Access applies the Default policy.
Step 3 – Change the DNS Settings on Your Relevant Network Device
You need only do this on your edge DNS equipment, typically a DNS or DHCP server, or a router—this could be your DSL router or cable modem if that's the only router in your network.
For instructions on how to configure computers (including laptops) or routers, see Point Your DNS to Cisco Secure Access.
Note: The client on which you test must have either retrieved a new set of DNS servers from the DNS/DHCP server or router, or have had its DNS settings changed manually for you to be able to verify successfully.
Step 4 – Test Your Network
Verify that your DNS connections are routed through Cisco Secure Access' global network by navigating to the following page in your client's browser: https://welcome.umbrella.com/. You should see the Welcome page.
Note: You may need to restart your client's network interface or your computer.
To test your security settings, navigate to http://examplemalwaredomain.com/.
Manage Identities < Add a Network Identity > Delete a Network Identity
Updated about 1 month ago
